Now Reading: Cyber Law in India – Meaning, Introduction, History, Need, Important terms and Amendments
-
01
Cyber Law in India – Meaning, Introduction, History, Need, Important terms and Amendments

Cyber Law in India – Meaning, Introduction, History, Need, Important terms and Amendments
What does Cyber Means?
A combining form meaning “computer,” “computer network,” or “virtual reality,” used in the formation of compound words.[1] Involving, using or relating to computers, especially the internet.[2]
Introduction to Cyber Laws
“Internet Law” is the well-defined area of law that suggests regulations to people about the use of the internet. Categorically cyber laws are divided into criminal laws and civil laws. Any law or regulation that involves how people use computers, smartphones, the internet and other related technology is cyber law.[3]
The virtual world of the internet is known as cyberspace and the laws governing this area are known as Cyber Laws and all the citizens of this space come under the ambit of these laws as it carries a kind of universal jurisdiction.
Cyberlaw is important because it touches almost all aspects of transactions and activities on and involving the internet, World Wide Web and cyberspace.
Cyberlaw encompasses laws relating to –
- Cybercrimes
- Electronic and digital signatures
- Intellectual property
- Data protection and privacy
History of Cyber Laws in India
The resolution of the General Assembly of United Nations dated 30th January 1997 gave birth to the Information Technology Act which leads to the adoption of Modern Law on Electronic Commerce on International Trade Law.
The Department of Electronics (DoE) in July 1998 drafted the bill. However, it could only be introduced in the House on December 16, 1999 when the new IT Ministry was formed. However it underwent some alteration with the commerce industry due to some suggestions related to e-commerce and matters about the World Trade Organization (WTO) obligations. After the bill was introduced in the Parliament, the bill was referred to the 42-member Parliamentary Standing Committee following demands and suggestions from the Members. One of the suggestions that was highly debated upon was that a cyber café owner must maintain a register to record the names and addresses of all people visiting his café and also a list of the websites that they surfed. This suggestion was made as an attempt to curb cybercrime and to facilitate speedy locating of a cyber-criminal. However, at the same time it was ridiculed, as it would invade upon a net surfer’s privacy and would not be economically viable. Finally, this suggestion was dropped by the IT Ministry in its final draft.[4]
Need for Cyber Laws in India
< p style="color: #0e101a;background: transparent;margin-top: 0pt;margin-bottom: 0pt;text-align: justify">In Techno-savvy world like today, People are becoming more digitally sophisticated. As time passed by it became more transactional with e-business, e-commerce, e-governance and e-procurement etc. All legal issues related to internet crime are dealt with through cyber laws.
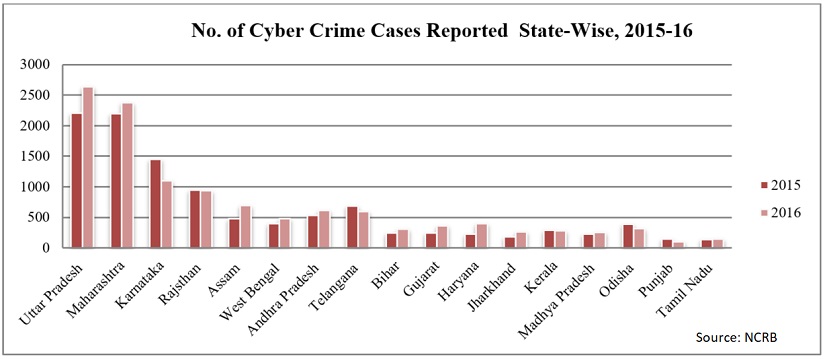
Number of Cyber Crime Cases Reported in the year 2015-16
Source- National Crime Record Bureau
In today’s highly digitalized world, almost everyone is affected by cyber law. For example.
•Almost all exchanges in shares are in Demat form.
•Almost all organizations widely rely on their PC systems, what’s more, keep their significant information in electronic form.
•Government structures including personal assessment forms, organization law structures and so on are presently filled in electronic forms.
•Consumers are progressively utilizing Visas for shopping.
•Most individuals are utilizing email, PDAs and SMS messages for communication.
•Even in “non-digital wrongdoing” cases, significant proof is found in
PCs/PDAs for example in instances of separation, murder, capturing, charge
avoidance, sorted out wrongdoing, psychological militant tasks, fake money, etc.
•Cyber wrongdoing cases, for example, web-based financial fakes, online offer exchanging extortion, source code burglary, Visa misrepresentation, tax avoidance, infection assaults.
•cyber damage, phishing assaults, email seizing, forswearing of administration, hacking, sex entertainment and so on are turning out to be common.[5]
Important terms related to cyber laws
“Affixing Electronic Signature” with its grammatical variations and cognate expressions means the adoption of any methodology or procedure by a person to authenticate an electronic record by means of Electronic Signature. (Sec.2(1)(d) of IT Act, 2000)
“Access” with its grammatical variations and cognate expressions means gaining entry into, instructing or communicating with the logical, arithmetical, or memory function resources of a computer, computer system or computer network. (Sec.2(1)(a) of IT Act, 2000)
“Asymmetric Crypto System” means a system of a secure key pair consisting of a private k
ey for creating a digital signature and a public key to verify the digital signature. (Sec.2(1)(f) of IT Act, 2000)
“Certifying Authority” means a person who has been granted a license to issue an Electronic Signature Certificate under section 24. (Sec.2(1)(g) of IT Act, 2000)
“Communication Device” means Cell Phones, Personal Digital Assistants (Sic), or combination of both or any other device used to communicate, send or transmit any text, video, audio, or image. (Sec.2(1)(ha) of IT Act, 2000)
“Computer” means any electronic, magnetic, optical or other high-speed data processing device or system which performs logical, arithmetic, and memory functions by manipulations of electronic, magnetic or optical impulses, and includes all input, output, processing, storage, computer software, or communication facilities which are connected or related to the computer in a computer system or computer network (Sec.2(1)(i) of IT Act, 2000)
“Computer Network” means the interconnection of one or more Computers or Computer systems or Communication device through-(i) the use of satellite, microwave, terrestrial line, wire, wireless or other communication media.
“Computer Resource” means computer, communication device, computer system, computer network, data, computer database or software. (Sec.2(1)(k) of IT Act, 2000)
“Computer System” means a device or collection of devices, including inputand output support devices and excluding calculators which are not programmable and capable of being used in conjunction with external files, which contain computer programs, electronic instructions, input data, and output data, that performs logic, arithmetic, data storage and retrieval, communication control and other functions. (Sec.2(1)(l) of IT Act, 2000)
“Cybercafe” means any facility from where access to the Internet is offered by any person in the ordinary course of business to the members of the public.
(Sec.2(1)(a) of IT Act, 2000)
“Cyber Security” means protecting information, equipment, devices, computer, Computer resources, communication devices, and information stored therein from unauthorized access, use, disclosure, disruption, modification or destruction.
(Sec.2(1)(nb) of IT Act, 2000)[6]
Amendments made in Indian Penal Code, 1860 by the IT Act, 2000
Amendments related to IPC were contained in Sec.91 and the First Schedule of the IT Act, 2000. Under the enactment of the Information Technology (Amendment) Act, 2008, Sec.91 was deleted and the provisions concerning the Indian Penal Code were mentioned in Part III of the amendment Act.
The amendments made to the Indian Penal Code are as follows –
1) Amendment to Sec.4 –
In section 4, – i) after clause (2), the following clause shall be inserted namely: – (3) any person in any place without and beyond India committing offense targeting a computer resource located in India ii) for the Explanation, the following Explanation shall be substituted, namely:- (a) the word “offense” includes every act committed outside India which, if committed in India would be punishable under this code. (b) the expression “computer resource” shall have the meaning assigned to it in clause (k) of subsection (1) of section 2 of the Information Technology Act, 2000.
2) Amendment of Sec.40 –
In clause (2), after the figure “117”, the figures “118,119 and 120” shall be inserted.
3) Amendment of Sec.118 –
In section 118, for the words “voluntarily conceals, by any act or illegal omission, the existence of a design”, the words “voluntarily conceals by any act or omission or by the use of encryption or any other information hiding tool, the existence of a design” shall be substituted.
4) Amendment of Sec.119 –
In section 119, for the words “voluntarily conceals, by any act or illegal omission, the existence of a design”, the words “voluntarily conceals by any act or omission or by the use of encryption or any other information hiding tool, the existence of a design” shall be substituted.
5) Amendment of Sec.464 –
In section 464, for the words “digital signature” wherever they occur, the words “electronic signature” shall be substituted.[7]
Amendments made in Indian Evidence,1872 Act by the IT Act,2000
Amendments related to the evidence Act were contained in Sec.92 and the Second Schedule of the IT Act, 2000. According to the enactment of the Information Technology (Amendment) Act, 2008, Sec.92 was deleted and the provisions concerning the Indian Evidence Act were mentioned in Part IV of the amendment Act.
1) Amendment of Sec.3 –
In section 3 relating to interpretation clause, in the paragraph appearing at the end, for the words “digital signature” and “Digital Signature Certificate”, the words “Electronic signature” and “Electronic Signature Certificate” shall be respectively substituted.
2) Insertion of new Sec.45A – Opinion of Examiner of Electronic evidence – 45A:
When in a proceeding, the Court has to form an opinion on any matter relating to any information transmitted or stored in any computer resource or any other electronic or digital form, the opinion of the Examiner of Electronic Evidence referred to in section 79A of the Information Technology Act, 2000, is a relevant fact. Explanation: For this section, an Examiner of Electronic Evidence shall be an expert
3) Amendment of Sec.47A –
In section 47A,- (i) for the words “digital signature”, the words “electronic signature” shall be substituted; (ii) for the words “Digital Signature Certificate”, the words “Electronic Signature Certificate” shall be substituted.
4) Amendment of Sec.67A –
In section 67 A, – for the words “digital signature”, the words “electronic signature” shall be substituted.
5) Amendment of Sec.85A –
In section 85A, for the words “digital signature”, wherever they occur, the words “electronic signature” shall be substituted.
6) Amendment of Sec.85B –
In section 85B, – for the words “digital signature”, wherever they occur, the words “electronic signature” shall be substituted.
7) Amendment of Sec.85C –
In section 85C, for the words “Digital Signature Certificate”, the words “Electronic Signature Certificate” shall be substituted.
8) Amendment of Sec.90A –
In section 90A, the words “digital signature”, at both places where they occur, the words “electronic signature” shall be substituted.[8]
[1] https://www.dictionary.com/browse/cyber- retrieved at 12:58 PM on 10 April 2020
[2] https://dictionary.cambridge.org/dictionary/english/cyber retrieved at 3:04 PM on 10 April 2020
[3] https://legalcareerpath.com/what-is-cyber-law/ retrieved at 5:19 PM on 10 April 2020
[4] http://www.indiancybersecurity.com/cyber_law/8_history_of_cyber_law_in_india.html retrieved at 8:45 PM on 10 April 2020
[5] http://www.legalserviceindia.com/legal/article-1019-importance-of-cyber-law-in-india.html retrieved at 2 PM on 11 April 2020
[6] http://www.indiancybersecurity.com/cyber_law/5_important_terms_related_to_cyber_law.html retrieved at 3:33 PM on 11 April 2020
[7]https://www.advocatekhoj.com/library/bareacts/informationtechnology/schedule1.php?Title=Information%20Technology%20Act&STitle=Amendments%20to%20the%20Indian%20Penal%20Code retrieved at 3:55 PM on 11 April 2020
[8] https://indiankanoon.org/doc/1953529/ retrieved at 1 PM on 12 April 2020